What are Honeypots

Many businesses currently depend on large quantities of data obtained across the internet through web scraping to implement business decisions. However, web scraping often confronts several challenges and, one such challenge is the honeypot traps. On the other hand, Honeypots are a vital asset to the Cybersecurity of your organization as well. So this article
Many businesses currently depend on large quantities of data obtained across the internet through web scraping to implement business decisions. However, web scraping often confronts several challenges and, one such challenge is the honeypot traps.
On the other hand, Honeypots are a vital asset to the Cybersecurity of your organization as well.
So this article will provide an overview of Honeypots before moving onto how you can avoid honeypot traps in web scraping.
What is a honeypot?
Honeypots in network security is a decoy system designed similar to a legitimate compromised system. Its primary objective is to bait cybercriminals into buying time and effort to exploit deliberate vulnerabilities to a computer system. It then alerts your in-house cybersecurity team of attackers’ compromised attempts.
This alertness would allow your security team to investigate the live attacks through honeypots to mitigate vulnerabilities and draw the attackers away from causing harm to the legitimate system.

How do honeypots work?
Since honeypots are identical to an actual computer system with application software and data to deceive cybercriminals, it is deliberately developed with security loopholes. A prominent example would be some vulnerable ports left open to lure attackers into the honeypot rather than the actual system.
Also, another honeypot scenario would be mimicking a Payment Gateway page on the internet, which would be an ideal target for cybercriminals for spying on credit card numbers. Once a cybercriminal lands on such a page, your security team can assess their behavior and track their movements to make the legitimate Payment Gateway more secure.
From the honeypots’ operation, you could consider it a valuable tool that helps identify security vulnerabilities to your organization and spot new threats. Furthermore, you would analyze attackers’ trends and introduce mechanisms to shield from such threats.
Different types of Honeypots
Honeypots can be categorized based on their deployment and involvement levels. Based on deployment, you can categorize them as:
Production honeypots – these honeypots are deployed alongside real production servers on your organization’s internal network. Its objective is to detect active attacks on the internal network and divert them from the legitimate server.
Research honeypots – in contrast, research honeypots are used to collect and analyze how an attacker would implement a potential attack on the system by analyzing their behavior. Through such analysis, the security team would be able to enhance the defense of the system.
Then based on the involvement levels, honeypots can be classified as follows:
Pure honeypots-these are full-scale production systems that appear to contain confidential or sensitive data. The security teams monitor the attackers’ intentions by the bug tap installed where the honeypots connect to the network.
High interaction honeypots- the primary purpose is to get the attacker to invest as much time as possible to infiltrate the security loopholes to attack the system. This would allow your cybersecurity teams to observe the attackers’ target within the system and discover its vulnerabilities. A typical example of a high interaction honeypot would be a Database.
Medium interaction honeypot- mimic the application layer without an Operating System so that the attacker gets confused or delays their mission. This would enable your security experts to buy time to respond to the attack in this scenario.
Low Interaction honeypot- These honeypots are easy to set up and use the TCP(Transmission Control Protocol), Internet Protocol (IP), and network services. They are less resource-intensive. Its primary focus is to simulate the systems that the attackers most commonly target. So the security experts Gather information on the type of attack and its point of origin. Security teams also use them for early detection mechanisms.
What are Honeynets?
So far, you have discovered a honeypot as a single Virtual Machine in a network. In contrast, honeynets are a series of honeypots networked together, as shown in the diagram below. A single honeypot is not sufficient to monitor suspicious traffic entering a more extensive network.
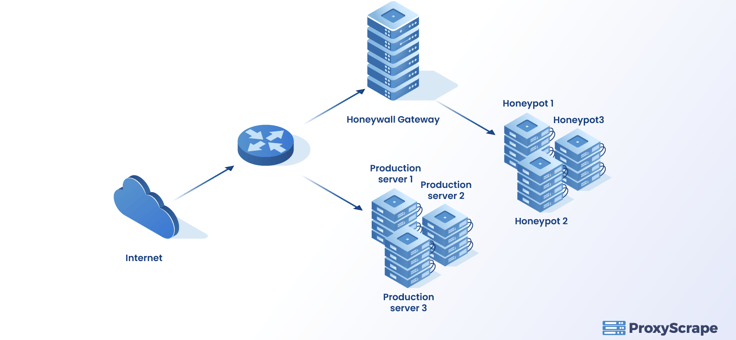
The honeynets are connected to the rest of the network through a “honeywall” gateway that monitors the traffic coming into the network and directs them to the honeypot nodes.
With the aid of honeynet, your security team can investigate cybersecurity threats of large-scale magnitudes, such as distributed denial of service (DDOS) attacks and ransomware. Then the security team can take relevant precautions to drive away the attackers from the actual system.
Honeynets protect your entire network from inbound and outbound suspicious traffic and are part of an extensive intrusion network.
Limitations of Honeypots
Now you may assume that with the presence of honeypots, your network is entirely secure. However, it is not the reality, as honeypots have several disadvantages and do not replace any security mechanism.
Honeypots can not detect all the security threats out there- just because a particular threat did not infiltrate the loopholes in the honeypot doesn’t mean that it would not enter the legitimate system. On the other hand, an expert hacker would determine a honeypot as illegitimate and attack other network systems, leaving the honeypot untouched.
An attacker could also execute spoof attacks to divert your attention from the actual exploit to your production environment.
Even worse, a more innovative hacker would use the honeypot as a way to gain entry to your production environment. This is the apparent reason why honeypots can not replace other security mechanisms such as firewalls. So since the honeypot can act as a launching pad to attack the rest of the system, you have to take adequate precaution to each honeypot in the network.
Honeypot traps in web Scraping
There are honeypot traps to avoid illegal web scraping, which implies just a handful of scrapers scraping copyrighted information. Unfortunately, due to these few scrapers, the legitimate scrapers too have to pay the price occasionally. This is because the honeypots are unable to distinguish legitimate scrapers from non-legitimate ones.
Web pages contain links that only the crawlers can access. So when a crawler scrapes data from those links, the website detects crawling activity. Thus, a website with honeypot traps can easily track and detect your web scraping activity as scraping from these sites is illegal. As a result, your IP is likely to get blocked, and therefore you will not get the desired data.
To bait the scrapers, some sites with honeypot links use their CSS display property to none. Therefore you have to make sure that your crawler follows only the visible links. Also, to avoid blocks, it’s best to follow the rules and guidelines of the website you are scraping.
Conclusion
Although the honeypots have certain risks, the benefits certainly outweigh the risks, as shown in the limitation section. Therefore honeypots are an essential mechanism to have when considering the security investment for your organization. Also, on the other hand, make sure that professionals with expertise are carrying out your security and honeypots assessments.