Certain use cases require you to proxy traffic in programs that do not natively support proxies. The previous blog discussed how this is possible on Windows, but there are also plenty of use cases for proxies on Linux or even Docker containers for added flexibility.
In this blog post, we will discuss how to use proxies for Docker containers using the xjasonlyu/tun2socks Docker container.
tun2socks is a lightweight and portable network tunneling tool that allows you to route traffic through a proxy server. It is written in Go and is available as a standalone executable or as a Docker container.
In this guide, I will focus on how to use it with Docker, so that you can then connect any other Docker container to it and make it use proxies.
First, we need to make an initial Docker container that will do the proxying.
docker run -d --name tun2socks \
-e EXTRA_COMMANDS='echo "nameserver 1.1.1.1" > /etc/resolv.conf;ip rule add iif lo ipproto udp dport 53 lookup main;' \
-e PROXY=http://<user>:<pass>@rp.proxyscrape.com:6060 \
-v '/dev/net/tun:/dev/net/tun' --cap-add=NET_ADMIN \
xjasonlyu/tun2socks
- EXTRA_COMMANDS is required for DNS to work properly since the tun2socks container does not handle DNS by default and only does the proxying itself.
- PROXY is where you set the Proxy that you want to use, this can be http/https and socks4/5. A detailed list exists here:
- -v '/dev/net/tun:/dev/net/tun' Mounts the host machine's virtual network device (/dev/net/tun) into the container, allowing tun2socks to manipulate network traffic.
- --cap-add=NET_ADMIN Grants the container the necessary network administration capabilities to establish the proxy tunnel by giving it access to the network stack.
In this example, I am using Proxyscrape residential proxies, but you can also use premium proxies or any other proxies as well.
Now that we have created the container that does the proxying, we can use any container we want to use this container’s network by just adding the --network=container:tun2socks flag.
To test if everything is working correctly, you can use a test container I built to return IPinfo location data.
docker run --rm --network=container:tun2socks hibenji/checkip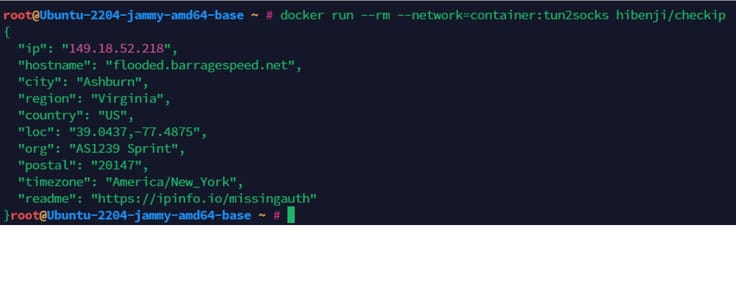
As you can see, we are now able to proxy pretty much anything through proxies, even when it's not natively supported.
Of course, you can use rotating proxies when creating the initial container, but you can also make multiple tun2socks containers, all having sticky sessions if that is required as well.
This approach to proxying in Docker opens up a world of possibilities. You can now use proxies in conjunction with practically any Docker container, even those without built-in proxy support. This can enhance the capabilities of your containerized applications, allowing you to perform tasks that might have been difficult or impossible without this level of network control.
Thanks for reading, and I hope you learned something!
This article was written by Benji, a ProxyScrape user.