Proxy Authentication – 2 Unique Ways
Proxy authentication allows the users to define authentication methods with which the users’ requests will be verified before getting processed. Statista says that 26% of global online users used proxy servers to access web content in the first quarter of 2018 which is expected to grow further in upcoming years. Users can authenticate the proxy
Proxy authentication allows the users to define authentication methods with which the users’ requests will be verified before getting processed. Statista says that 26% of global online users used proxy servers to access web content in the first quarter of 2018 which is expected to grow further in upcoming years. Users can authenticate the proxy access with certain credentials to ensure that they are authorized users. This article will guide you by explaining the ways to authenticate a proxy.
Table of Contents
- What is Proxy Authentication?
- How Does Proxy Authentication Work?
- Two Methods of Proxy Authentication
- HTTP Proxy-Authenticate Message
- HTTP 407 Response Message
- Frequently Asked Questions
- Final Thoughts
What is Proxy Authentication?
Proxy authentication enables you to configure the authentication method the proxy server uses and determines how to validate client machines when accessing proxies. By default, the proxy authentication field is disabled and must be enabled to create new policies for users or groups.
How Does Proxy Authentication Work?
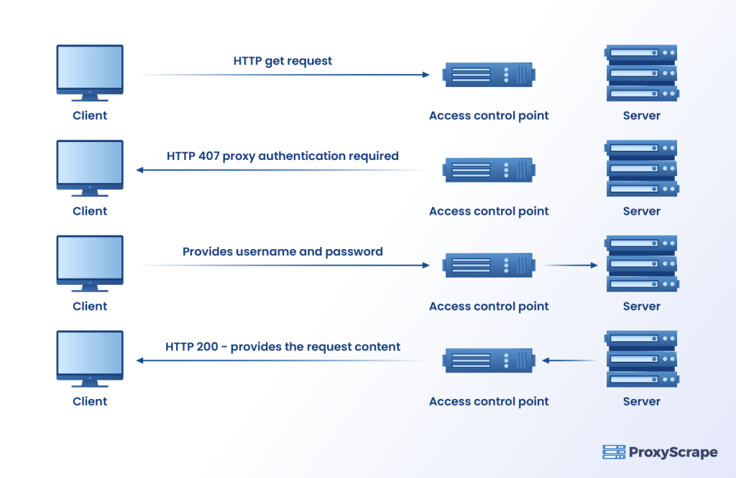
Proxy authentication validates and verifies a client’s request. The proxies also serve as access-control devices blocking requests until the user or the client provides valid access-permission credentials to the proxy. The HTTP proxy-authenticate header defines the authentication method required to access the resources from the proxy server.
The Hypertext Transfer Protocol (HTTP) provides a framework for communication between the client and the proxy server. The client sends additional information about the request and the client to the server through the HTTP request header field. The proxy server requests credentials for validation through the header message in the HTTP response message.
Two Methods of Proxy Authentication
There are two methods of proxy authentication. The first type is authentication using a username and password and the other one is authentication through an IP address. During signup, the proxy provider offers a username and password along with a set of proxies. Once you purchase the proxy package, you must set up a username and password and once the payment process is over, you receive a confirmation mail along with the list of proxies.
Proxy Authentication via Username & Password
Users must log in with a username and password to ensure that authorized users have access to the residential proxies. The users create these credentials with the basic authentication method and mention them in the HTTP request in the Proxy-Authentication header.
Users utilize this credential to access all proxies from their pool of proxies. For enhanced security, credentials are set for every single proxy, which works well with residential proxies for accessing geo-specific proxies.
This is a sample mail of how proxies are sent through the mail with IP address and port number. The username and password are used to authenticate the proxies.
| Hello,Here are your proxies.Ip:port:user:pass176.123.25.31:80:dedica123:walker176.123.12.224:80:dedica123:walker89.36.65.33:80:dedica123:walker104.143.28.208:80:dedica123:walker104.143.28.248:80:dedica123:walker104.142.28.215:80:dedica123:walker89.36.65.138:80:dedica123:walker176.123.25.50:80:dedica123:walker176.123.12.197:80:dedica123:walker104.143.28.250:80:dedica123:walker |
Proxy Authentication using IP address
The most secure method of authentication is using an IP address. You require the IP and port in the proxy settings if you set IP authentication. You can configure your browser’s IP address which you use to scrape the client, so it’s best to include your IP address on the dashboard of the proxy providers or through the service API.
By doing so, you are whitelisting your IP address with the proxy provider allowing you to access proxies without a username or a password.
Whitelisting is the process of allowing pre-approved IP addresses to access the proxies. Instead of sending a proxy-authentication header, you use your IP address to access the proxies. HTTPS requests with web browsers or testing with Selenium are also easy as there is no proxy-authentication header.
HTTP Proxy-Authenticate Message
The primary function of the Proxy-Authenticate header is to access files and folders from the server. Users utilize the header when a user requests confidential information. The related HTTP status code to request the user’s credentials is “407” which means “Proxy-Authentication Required.”
This HTTP proxy-authenticate message with status code 407 is a response message to the client from the server and is an authorization method followed by the server to validate when the client requests a proxy.
A server sends this message when it cannot complete a request due to the lack of proper authorization credentials. The client sends the requested credentials and the server after the validation provides the client’s requests.
HTTP 407 Response Message
When a user requests proxies to scrape a website, the proxy server first issues a 407 proxy-authorization status code demanding access credentials. The user receives the 407 response message and it gathers the necessary credentials either from a local database or by prompting the user.
The client then resends the HTTP request message with the credentials from a proxy-authorization header field. If the credentials are valid, then the user may access the proxies, otherwise, it sends another 407 request message.
Proxy-authenticate HTTP request header provides credentials for auditing to support proxy server verification.
Have a look at this blog “Proxy Errors – 5 Categories And Solutions” that lists the status code and undertsand what each code mean and how to fix it.
Syntax
Proxy-Authenticate:<type>realm=<realm>
The directive <type> is one of the authentication schemes the Internet Assigned Numbers Authority (IANA) mentions. The most common authentication type is Basic, which accepts a username and password to authenticate the client.
The directive <realm> describes the protected area, which is usually a website that a client wants to access.
Related Articles
How To Use A Proxy With Python Request
How To Build An HTTP Proxy In Python
Frequently Asked Questions
1. Why do you need proxy authentication?
Proxy authentication is necessary when a client accesses a website through a proxy server that enables access control features for security purposes and the website sends a 407 HTTP response requesting credentials from the client.
Proxy authentication enables you to configure the authentication method the proxy uses, which determines how it validates client machines when accessing the target website.
2. What are the different HTTP headers?
There are four types of HTTP headers: They are General Header, Request Header, Response Header, and Entity Header.
3. What are the limitations of using IP authentication?
- In IP authentication, access to the proxy depends on the IP address.
- You must authenticate a new IP address if the proxy provider uses a dynamic IP system that allows you to change your IP address.
- Repeated failed login attempts can cause temporary IP address blocks and you must wait until the block starts using the IP again.
- The proxy system does not allow authentication to the same IP address for multiple accounts.
Final Thoughts
Proxies validate users before processing their requests and make use of the basic authentication method of providing the username, password, and IP authentication. ProxyScrape offers data center, premium, and residential proxies of which the data center and premium proxies support IP authentication and usernames and passwords authenticate residential proxies.
The residential proxies are best for accessing geo-specific content, as the authentication is simple. You may perform it by providing a username and password. Do you wish to know more about proxies and their different types? We have flexible plans that would suit your business and you may visit our website to learn more about them.