What is Browser Fingerprinting and How to Avoid It?
When browsing the internet, privacy should be your primary concern. As you’re already aware, websites employ various mechanisms to track your online identity; include recording your IP address, storing cookies on your browser, HTML 5 Canvas to name a few. You can easily mask your online identity by using proxies or deleting cookies on your
When browsing the internet, privacy should be your primary concern. As you’re already aware, websites employ various mechanisms to track your online identity; include recording your IP address, storing cookies on your browser, HTML 5 Canvas to name a few.
You can easily mask your online identity by using proxies or deleting cookies on your browser. However, did you know that there are other ways to keep an eye on you which are impossible to prevent in the first place? One such technique that we will discuss in this article is browser fingerprinting and what you can do to avoid it.
So without further ado, let’s get started.
What is browser fingerprinting?
Whenever you connect to a website, its server would collect information about your browser to identify you. Obviously, fingerprinting doesn’t mean that the receiving server would identify you by your name or your IP address. Instead, it would use the information in your browser as well as your device settings.
In general, some of these settings include browser type and version, operating system information, active plugins, screen resolution, time zone, and various header information that we will discuss below. Also, the browsers can send information about your browsing history.

What information does a website gather for browser fingerprinting?
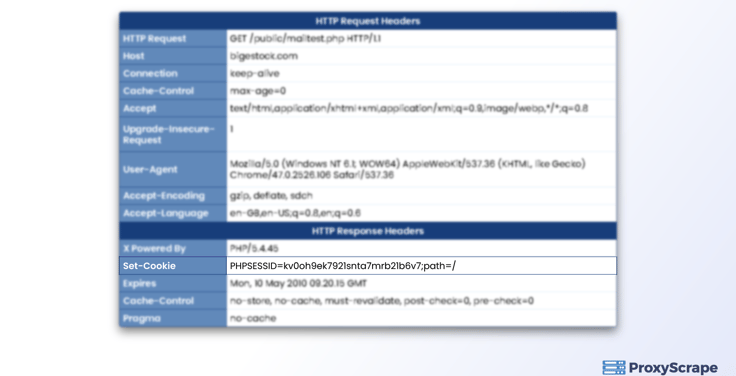
Headers
When you connect to a website, there will be several headers that your browser sends to the receiving server. They are:
- Connection header- determines whether the connection to a web page is an open or close connection.
- User-agent header – this header sends the information about your browser and Operating system. You can find further details on the user-agent here.
- Language header- the language that your computer system uses
- Content encoding header – lists the compression type that your computer system handles.
- Accept header- provides the receiving website with the type of content that your browser would display.
- Cache-control header – provides instructions to the receiver server on how data should be cached on the front-end and back-end.
- Referrer header – this header tells the receiving website from which website you clicked its link.
- Upgrade insecure header – provides details on whether your browser is requesting an encrypted connection or otherwise
So at first glance, the above data may seem generic, as it may not appear to identify a person aka browser uniquely. However, according to Panoptickclick, only 1 in 286,777 will share the same fingerprint as another user. As you can see from the above header information itself, your browser creates a fingerprint that uniquely identifies you.
Additional browser information
Some of the additional browser information included in the browser fingerprint includes:
The build ID of the browser: this ID tells the receiving website about the version of your browser. However, when you use a secure browser, you would be able to mask this information.
Cookies: They’re small packets of text data that uniquely identify you when you’re connected to a computer network. For further information about cookies, read here.
Ad preferences: Ad preferences such as “Do Not Track” tell the receiving website not to track your information. When you decide to turn it on, your browser can send your information to analytic companies, websites, plugin providers, and other web services you visit while browsing the internet.
Ad Blocker: Browser will pass the information whether the Ad Blocker is on or off.
HTML 5 Canvas Image: For websites coded with HTML 5, canvas elements generated data such as font size and background color of visitors’ browsers.
Now you may wonder why websites collect your browser fingerprint. It is what the next section is all about.
Why do websites collect your browser fingerprint?
You don’t need to fear as with all the above information, it’s impossible to know your name and address. However, these browser fingerprints are of great value to companies when advertising their products to different segments in a market. After all, international advertisers and marketers love these fingerprint data, and they would do anything to get their hands on them.
Based on your data, it is easier for marketers and advertisers to target potential customers in a specific geographical area, for instance. So while fingerprinting can be an inconvenience to you, there are positive aspects of it as well—more on this in the next section.
Why is browser fingerprinting essential in certain circumstances?
Now you have gained fundamental knowledge on browser fingerprinting and why it is used. The following section will provide you with an overview of why you need browser fingerprinting in certain situations.
It helps to prevent online financial frauds
For instance, browser fingerprinting helps determine whether a bank account has been accessed several times from multiple locations/browsers in web banking within a short period. In addition, it also helps to determine if a hacker has hacked browser sessions.
Identifying hacked browser sessions would help track the hackers who steal login credentials and credit card numbers. Ultimately if the fraudsters change their devices with several attempts to log in, the security experts could easily detect them.
Prevents eCommerce fraud
Most of the eCommerce transactions take place in the form of wire transfers. At the same time, other eCommerce transactions take place from predictable devices. So when there is a sudden change in the source, security experts can detect fraud without a doubt.
What are the drawbacks of browser fingerprinting?
Violates current privacy regulations- Large percentage of the users are not aware of the quantity of data transferred for browser fingerprinting. It’s also unclear to whose hands these data would get into. As you’re about to discover in the next section, browser fingerprinting can not be quickly deleted, just like cookies.
Malicious websites – Most well-reputed websites may use traditional marketing over browser fingerprinting to market their products. So most of the websites that do collect browser fingerprinting can be classified as spam malicious sites. Therefore there is a risk of essential information falling into the wrong hands.
How can you avoid browser fingerprinting?
So far, you have an understanding of the type of data that a browser uses for fingerprinting as well as its pros and cons. Now it’s time to dive into an all-important factor of how you’re going to stop it. Let’s dive in, folks.
Disable JavaScript

JavaScript is a front-end scripting language that works at the browser level. It is mainly used for enhanced user experience, as well as coding specific scenarios of responsive web design. When you disable it, your browser cannot send information about plugins, extensions, fonts and cannot install cookies in your browser.
However, disabling JavaScript may not be a feasible solution for some websites that are heavily reliant on JavaScript. In contrast, other websites may work just fine without it. However, there is a better solution to which we will discuss below so that the user experience is not compromised.
Manage browser extensions and plugins
Although browser extensions and plugins are great assets for your browsing experience, they can also hinder your privacy. This is because they can track you, as mentioned above.
The more browser extensions and fingerprints your browser has, the more unique your browser fingerprint would be. This is a scenario that you don’t wish to fall into. Therefore you need to uninstall the extensions and plugins that you don’t need.
In addition, you need to be cautious that merely uninstalling the plugins will not help you overcome being traced. This is because they’re still on your device. So an enhanced option would be to use JavaScript disabling extensions.
Use a VPN
Using a Virtual Private Network (VPN) creates a secure connection between your device and the VPN. After that, VPN connects to the target website forwarding all the traffic on your behalf. Throughout the entire process, the communication passes through an encrypted channel. This ensures that hackers can not intercept your messages, and your IP address will be masked.
Despite these secure means, VPN still can not disable JavaScript as well as sending header information. So your browser still can create a unique fingerprint taking out the IP address from the equation.
Use Incognito mode
Another way of masking your identity would be to use Incognito mode. It would set the headers and browser profile to its default settings, making it difficult to track your information.
To determine if it operates correctly, you can check with this browser fingerprinting checker when your browser is set to Incognito mode.
Use the Tor browser
Did you know that the Tor browser doesn’t store any browser information and automatically deletes cookies? Furthermore, the Tor browser aggressively blocks JavaScript code on websites, avoids third-party ad-tracking, disables time zone and language preferences.
Without the settings mentioned above, it would be harder to create a fingerprint of your browser. In addition, Tor says in their fingerprinting terms that, by default, all their users will be set to the “same as all users” when creating the fingerprint.
Install Anti-Malware Software
The presence of anti-malware software on your computer not only protects it from malicious acts. But also from obscuring your browser fingerprint. You must ensure that it is updated with the latest threats in your system at all times.
In most circumstances, anti-malware blocks ads, malicious and irritating toolbars, and other malicious code or spyware that could be operating in the background.
The browser fingerprint is directly linked to the software and tools mentioned above. As a result, it is essential to have a clean browser and delete the threats with an anti-malware tool.
Other techniques to avoid browser fingerprinting
You have discovered in the previous section that disabling JavaScript would prevent your browser from fingerprinting certain information. However, this would compromise user experience, particularly for websites that are heavily dependent on JavaScript.
So to sustain the user experience, you can use a particular technique called spoofing which we will discuss below:
User agent spoofing
User-agent spoofing is faking the user-agent string that the browser sends to the receiving web server. This may not be the most innovative technique, but it certainly helps if you do not wish to reveal your identity.
The most effective way to spoof a user-agent would be to use rotating user-agents; this implies that you will have a different user-agent string after a specific time interval. This method scores well over using static user agents.
A prominent example of a rotating user agent is the Chameleon browser.
Spoof your Canvas API
Canvas is an HTML5 tag that was initially intended to draw graphics on web pages. But various browsers interpret it differently. As mentioned previously, HTML5 Canvas generates data such as the background color and font size of a visitor’s browser, which serves as a unique fingerprint for each visitor. So unlike cookies, you will not be able to delete the canvas data as it’s not stored on your computer.
So the only way to eliminate the Canvas out of the fingerprint equation is by using a CanvasBlocker. It blocks the calls to Canvas API.
Virtual Machine
Having a Virtual Machine (VM) is another method that leads to a fake browser fingerprint. When you use a VM to browse the internet, the VM’s browser fingerprint would be generated. This browser fingerprint will be different from your actual browser. Some of the prominent examples of VMs include Oracle VM Virtualbox, and Parallel Desktop, among others.

Conclusion
Now, this article has provided you a comprehensive overview of what browser fingerprinting is and how it can be avoided. While users generally consent that browser fingerprinting is harmful and in some situations unethical, there are no signs of it ending soon.
Therefore you would have to employ some of the methods mentioned in this article to prevent browser fingerprinting information from falling into the wrong hands. Since browser fingerprinting also has pros, it’s best to choose a balanced approach to your needs.