Cloud Proxies and their 4 Use Cases
Cloud proxies can benefit people with huge potential by integrating the cloud and proxy features. Cloudwards estimates that, by 2025, there will be 100 zettabytes of data stored in the cloud. As people prefer the cloud medium to store and host their services, integrating the cloud with a proxy can take the performance to the
Cloud proxies can benefit people with huge potential by integrating the cloud and proxy features. Cloudwards estimates that, by 2025, there will be 100 zettabytes of data stored in the cloud. As people prefer the cloud medium to store and host their services, integrating the cloud with a proxy can take the performance to the next level. This article will focus on the Cloud Proxy, its security features, and its impact on proxy users.
Table of Contents
- What Are Cloud Proxies?
- Why Use Cloud Proxies?
- Proxy Appliances
- Drawbacks of Proxy Appliances
- Steps to Consider Before Moving to Cloud Proxies?
- How Do They Work?
- Proxy-Based CASB
- Benefits of Cloud Proxies
- Drawbacks of Cloud Proxies
- Use Cases of Cloud Proxies
- Frequently Asked Questions
- Conclusion
What Are Cloud Proxies?
A cloud proxy is an intermediate cloud component that acts on behalf of the client and communicates with the web server. Usually, the proxy servers can be anything like software, devices, or web browsers that hide the actual identities of users with their own identities. But in the case of cloud proxy, the proxy becomes a virtual address that reroutes the client information with their own proxy address.
Proxy servers with their advanced features have secured a pivotal place in this digital era. People prefer using proxies to fulfill their business requirements or personal computational needs. Running these proxies in a cloud environment further amplifies the proxy capabilities to multiple folds.
Why Use Cloud Proxies?
Those were the days when people relied more on paper documentation. Later on, storage devices stored and retrieved data from a secondary device or from the device itself. People aren’t normal web users anymore. Users now try web scraping with the help of proxies, which are not easy for normal users to do. When user requirements grow, so does the size of the data. To cope with the high-speed data generation, we prefer virtual space, like the cloud. Proxies function better in a cloud environment when handling heavy and complex proxy operations.
Cloud Proxies are proxies that work in a virtual environment and not on physical devices, as does a data center. Proxies are the intermediary component that acts on behalf of a node by protecting its identity and hiding the IP address from the network.
Proxy Appliances
Proxy appliances are the usual hardware devices that act as an intermediate between the nodes that are involved in client-server communication. These proxy appliances work for either side of the communication. Some proxies mainly intend to prevent the clients from IP bans while others concentrate on keeping the server identity under wraps. These proxies provide device-level storage and help people to extract huge piles of data in no time with zero restrictions.
Drawbacks of Proxy Appliances
- Though the device-level proxies promise high-security features., they can not match the cloud-based security features.
- This type of proxy server may bring in performance and usability issues when handling a huge number of complex processes or unexpected behavior.
- Proxy appliances may face compatibility issues with some applications that only support advanced virtual storage models.
- Proxy appliances are highly memory-consuming as they require more memory for the data caching process.
- The installation costs and the SSL encryption process require 8 times the usual cost.
- They lack in providing an attractive user experience.
- The backup may cost twice the resources, setup, and maintenance costs.
Steps to Consider Before Moving to Cloud Proxies?
- Check whether the business or project can handle the scaling up and scaling down process. Analyze the scalability need of the project and choose a suitable cloud environment per the requirements.
- Make sure the system faces no system support issues. The cloud proxy should run well with all sorts of configurations and application traffic.
- Make a necessary backup storage plan in case the system is down for some time.
- The cloud proxy should possess the capacity of solving complex problems and handling cloud-based applications.
- Plan for an economic cloud setup and maintenance by selecting suitable resources.
- Make sure the cloud proxy can provide users with clean and quality traffic to improve the user experience.
How Do They Work?
The prime functionality of a cloud proxy is to keep track of users. The cloud proxy monitors and decides whether to allow users to the site or not. They decide based on the company policies. This detailed analysis and security measures enhance the quality of the user experience. They eliminate the unnecessary crowd in the site and make the place safe for consumption. Building a proxy-based security architecture in the cloud protects all the protocols and requests from attackers.
Proxy-Based CASB
The Cloud Access Security Broker (CASB) is a cloud-based security system that acts as an intermediary between the cloud user and the cloud provider. There are a few types of CASB. Among them, the proxy-based CASB is the CASB that works in a proxy mode. It furnishes all the features of proxies along with high-level cloud security goals.
Working of CASB – Cloud Proxies
In this method, the internet traffic from the cloud environment variables passes through the CASB in proxy mode. The CASB in proxy mode performs user authentication, encrypts the data, filters the URL using the proxy-based security features, and takes the risk management decision. This supports the system in providing a quality experience to the users by filtering the bad traffic. They undergo a user authentication check to know whether the user’s browser passes all the company policies and ensures a highly secured environment. After the real-time security check from the proxies, the traffic passes to the SaaS services. Proxyscrape is a proxy provider solution that furnishes proxies that are capable to work with CASB.
Benefits of Cloud Proxies
- Using the proxy features and services at the cloud level increases the quality of the user experience. The user can make use of the proxies’ security goals scraping features in cloud-based environment variables.
- Apart from using proxies for fixed locations, the cloud proxies support changing locations and sometimes roaming locations too.
- The cloud proxy is capable of expanding the features by including additional security features with API integration.
- This cloud proxy is capable of handling all sorts of traffic and cleaning unwanted network traffic.
- Cloud services work on a pay-per-use model. Here, we can pay only for the things which we use.
- As the cloud proxy model is independent of the physical hardware devices, it is easy to promote the anonymity and security of the cloud proxy users.
Drawbacks of Cloud Proxies
- One major drawback of cloud proxy is that the industry is coming across new technologies to incorporate with the cloud.
- As cloud API integration is faster than proxy-based clouds, service providers like Microsoft do not recommend proxy-based cloud applications though they do not ban them.
Use Cases of Cloud Proxies
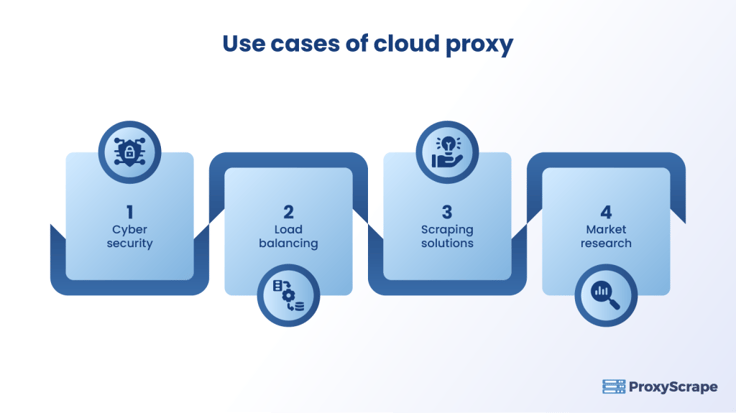
Use Cases of Cloud Proxies
Cloud Proxies are implemented in most applications these days. Here are some of the domains that primarily rely on cloud proxies.
Cyber Security
The cloud environment has higher opportunities for getting exposed to cyber threats. In this case, proxies help network users to ensure anonymity as all the incoming messages must undergo a proxy gateway before reaching the other end. The proxy makes use of encryption techniques to encrypt and decrypt messages.
Related Articles
Web Scraping and Cyber Security
Load Balancing
Web servers may become at risk for crashes with too many request loads. The possibility of this issue can double in a cloud environment. To deal with this issue, proxies distribute loads to the servers nearer to the clients to balance the load, so the main server and other servers do not get into trouble. Another case is that the web server prefers to stay anonymous so that it can stay safe from attackers. In this case, the load balancers use reverse proxy techniques to distribute the requests among supporting servers.
People Also Read
Reverse Proxy And Its Functionalities
Scraping Solutions
Business marketing professionals and data analysts require tons of data from a wide array of resources. When the data is stored in a cloud environment, scraping becomes even easier to store in the virtual database. To cope with the increased efficiency of the cloud solution, a proxy becomes the most necessary component to scrape unlimited data at high speed without IP restrictions.
Also, Reads
Market Research
Analyzing a huge set of data across the globe is the primary need of a business. This analysis can help marketers to come up with ideas that work for their increased sales. Cloud-based scraping tools can easily fetch and process data from various sites without geographical restrictions. To overcome these IP blocks and geo-block issues, cloud proxies may be the right choice.
Frequently Asked Questions
FAQs:
1. What is a cloud proxy?
2. How will a cloud proxy help my business?
3. Is it necessary to choose a cloud proxy?
Conclusion
Cloud proxy is the one unique solution that we have discussed so far. If you focus more on securing proxy services for your system through highly optimized virtual memory, you can choose cloud proxy. Though it has some shortcomings like speed, this is most suitable for proxy users to enhance their scraping operations. Proxy-based CASB will be the best choice for cloud users to protect their systems from hackers. Proxyscrape is one of the reliable proxy vendors that provide proxies that can work well for the cloud proxy setup with high speed and bandwidth. They provide rotating residential proxies so that the users can make use of rotating IPs from the proxy pool. Check out the proxy prices for your desired location.